What’s Next for IIoT Device Connectivity?
The Industrial Internet of Things (IIoT) has not only blurred the lines between OT and IT disciplines but also led to the increasing prevalence of large-scale and highly distributed applications where field devices are dispersed over a wide area and need to communicate directly with remote servers.
This means that where your data is going to and from, how you manage all your different devices, and how you keep your data safe matter even more than before.
This article provides three expert tips you should keep in mind for selecting device connectivity solutions that can meet the demanding requirements of large-scale and highly distributed IIoT applications in our connected world.
Know Where Your Data Goes
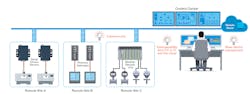
Large-scale and highly distributed IIoT applications need to collect data from many different sites. Just imagine all the wellheads in a typical oil-drilling application that could be spread out over a massive desert. All the data from each wellhead not only needs to be collected and constantly monitored and controlled from afar but also needs to be sent somewhere to process all the digital bits of information into human-readable insights.
You could deploy an edge computer at each field site to collect, locally preprocess, and transmit your data to a remote server for more advanced analysis. However, some applications may only need to enable connectivity and be able to sufficiently process their data on a cloud server.
Using connectivity devices at each IIoT field site to transmit your OT data to a remote server could save you time, effort, and costs. That is because many distributed applications, such as oil drilling, only require collecting relatively small amounts of data from each field site, so the costs and programming effort associated with deploying edge computers at multiple locations may not be justified. Instead, connectivity devices can usually do the trick and be more cost-effective and efficient too.
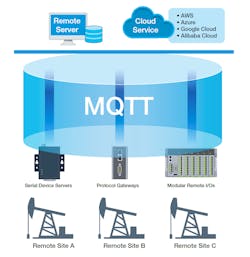
You’ll also want to consider the type of remote server you’re working with. For private servers, MQTT is one of the most commonly used protocols to bridge the data between OT and IT systems. As for public cloud servers—such as Microsoft Azure, Amazon Web Services (AWS), or Google Cloud—each service provider has its own methods and protocols for collecting data.
Before you choose your connected devices, you should know (or decide) whether your applications use private or public servers, and then find the connectivity devices that support related protocols or SDKs to save you time and money in the development stage.
Stay on Top of Device Management
When you finally get all your field devices with multiple communication interfaces connected, another big question arises. How do you manage dozens or hundreds of different kinds of connectivity devices?
During your daily operations, you need to monitor your connected devices to keep them up-to-date with the latest firmware and minimize unauthorized access and potential intrusions by updating device logon credentials for every user.
Such tasks might not be an issue when there are only a few devices and one type of connectivity device. However, it can be a huge burden if dozens of different kinds of connectivity devices are used in your IIoT application.
Having a software tool or utility that can help you manage large amounts of different kinds of connectivity devices can make daily operation much easier. With the lines between the IT and OT worlds becoming increasingly blurry in the IIoT era, management tools need to be flexible enough to serve users from both domains.
Besides mass device management capabilities, the connectivity device you choose should have both a GUI for OT users and CLI for IT users to optimize IIoT system maintenance.
As Always, Cybersecurity Matters
The diversity of end devices in industrial field sites, distributed architectures, and legacy systems increases the security risk of your IIoT applications because most of these devices are not designed with cybersecurity in mind. As a result, it's essential to select connectivity solutions with built-in security features to place in front of your end devices.
But with so many connectivity solutions on the market to fulfill the communication demands of different edge devices, how can you ensure your field data is well protected? Enter the IEC 62443 standard, a set of global security guidelines that list specific security requirements for device manufacturers to follow to ensure the device you choose meets the latest cybersecurity standards.
When you choose a connectivity device, use the following checklist to make sure the devices support sufficient security features and allow you to define and control user access to your IIoT applications.
- Identify and control who can log on to devices
- Increase password complexity to enhance access control
- Verify authorized devices before the devices gain access to the network and communicate with other devices
- Encrypt confidential serial interface data on the network to ensure data integrity
- Encrypt configuration data to increase confidentiality
- Select device vendors that respond quickly to and fix reported vulnerabilities
Keep the above three tips in mind so that enabling device connectivity for your IIoT applications can be easier, more secure, and more efficient.
To help you get started, Moxa has developed a series of device connectivity solutions, including serial device servers, protocol gateways, and remote I/O devices, that are capable of connecting your field data to private or public servers securely and efficiently.