Cybersecurity device manufacturer SonicWall has about 1 million units in the field, each one a sentry always on the lookout for malware attempting to infiltrate enterprise systems. In 2017, the SonicWall Capture Labs team says these firewalls out in the field logged 9.32 billion attacks, an average of 25 attempted attacks per day per device.
While big-name “celebrity” malware, such as WannaCry or Mirai DDoS botnet, or the Intel processor exploit known as Meltdown, make the most headlines, the next major threat to your company might be a completely unknown strain. And if you aren’t protected, the results could be catastrophic.
“One could impact a business by $1 or 2 million,” says SonicWall CMO Bob VanKirk, referring to if a production line was brought down, which did happen to Renault during the WannaCry attack. “How many businesses can weather that and come out the other side? Can they really afford to be down for a week or two?”
Those are worst-case scenarios, and maybe you’ll catch it in time to mitigate the damage. But cyber-attacks should be seen less like getting struck by lightning and more like cancer. In March, nearly a year after WannaCry’s patches came out, Boeing found the virus, believed to be a stolen NSA exploit, in their South Carolina plant.
“It is metastasizing rapidly out of North Charleston and I just heard 777 [automated spar assembly tools] may have gone down,” wrote chief engineer Mike VanderWel to employees. By that evening, all was contained and no severe damage was done.
But that’s one of the world’s most advanced companies patching a well-known virus. It won’t always be that easy. The 2018 SonicWall Cyber Threat Report found a 101% increase in malware variants, despite the number of detected ransomware attacks dropping from 638 million to 184 million.
“The security landscape is changing at a torrid pace,” says SonicWall CMO Bob VanKirk. “In some cases, we see versions of ransomware morphing twice a day. It really takes a level of sophistication to be able to understand this and protect an organization properly.”
What’s more, the attack surface expands every time a company connects a new sensor or piece of equipment to their Industrial Internet of Things network. The Capture Team’s also identified encrypted traffic as a possible channel for new threats, because they can bypass traditional security controls.
“We are in a cyber arms race,” VanKirk says. “There have been advances on the good side, but we recognize there are constantly advances on the cyber-criminal side.”
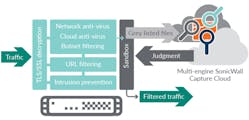
SonicWall believes the only way to stay one step ahead, especially for businesses that can’t afford a dedicated IT team, is by using automated real-time breach detection and prevention. They developed their next-generation SonicWall Capture Cloud Platform with the intent not to barely outrun attackers, but to lap them and give a swift kick in the behind as they pass by.
The platform features integrated threat intelligence, workflow automation, zero-touch deployment, flexible reporting, intelligence-driven analytics, and scalable cloud architecture.
“When you look at the number of attacks, you really need to have something that leverages machine learning AI to handle that amount of volume and new variants that are constantly coming out,” VanKirk says.
The platform’s strongest new tool to do this is called the Real-Time Deep Memory Inspection Technology and Engine (RTDMI). The proprietary innovation, employed in the Capture Advanced Threat Protection (ATP) service catches and quarantines infected files, such as Meltdown exploits, mass-market, zero-day threats, and unknown malware. It works by pulling an Inception-level trick on the bad bug, making it think a sandboxed “dream” is the real operating system.
“At a very high level, it takes an unknown file, loads it into a sandbox, then using a variety of automated techniques, our systems basically fast forwards the application to look for flaws,” explains John Gordineer, director of product marketing, and former product line manager at the company.
The RDTDMI sometimes has less than a 100-nanosecond window to detect the malware’s weaponry.
“A lot of times malware will try to evade detection,” Gordineer says. “If it determines it’s in a sandbox environment, it will refuse to detonate. By using memory, we can force it to reveal all of its techniques. We basically take over that application like it’s a puppet and make it do whatever we want it to do.”
Like its hardware, SonicWall says its Capture Cloud Platform is affordable for mid-tier manufacturers to optimize its array of firewalls. You know you probably will need it someday, just like a 22-year-old knows they will need health insurance someday. But if you feel great and none of your friends are sick, you risk it.
Grown adults, though, are forced to look at the worst case, and with cyberattacks, even a tiny exploit can shatter a giant operation.
“If Meltdown gets into the IoT infrastructure, it can be catastrophic,” VanKirk says.